Security Automation In Action
See examples of how intelligent automation can improve the efficiency and performance of securing IT and OT environments
See examples of how intelligent automation can improve the efficiency and performance of securing IT and OT environments

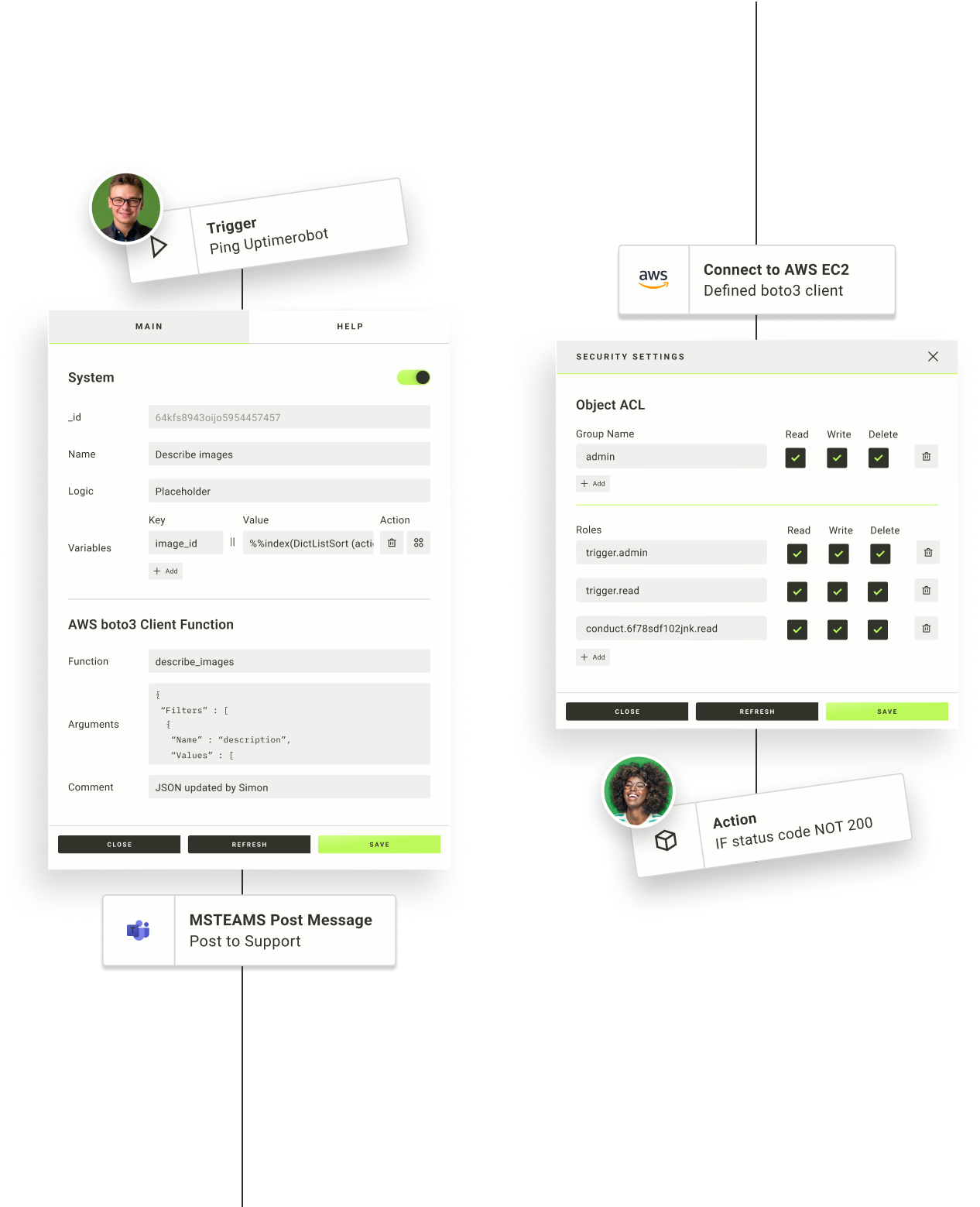
Automate IT security responses to improve incident resolution times. Build automated workflows that significantly reduce the need for manual intervention to save time, minimise disruption, and cut the risk of human error.
Accelerate incident resolution with automated workflows
Reduce client disruption
Deliver a positive outcome
Monitor your organisation's external perimeter for potential vulnerabilities. Add any specified ranges and domains owned by your organisation to the asset database for discovery landscape mapping. Scan assets for open ports and web-facing applications, and analyse security headers, updating a real-time dashboard to show the current state of the organisation's external attack surface.
Monitor your company's external attack surface
Automatically identify, scan, and analyse external assets
Stay informed via a real-time dashboard
Audit the strength of compromised passwords for ISO27001 compliance. Extract password hashes from your organisation's Active Directory accounts. Utilise A-Ops' AWS integration to build a segregated environment to securely pen-test users' passwords with wordlists used by hackers. Upload analysis of compromised passwords to a dashboard for a real-time overview of the state of your organisation's Active Directory
Accelerate incident resolution with automated workflows
Reduce client disruption
Deliver a positive outcome
Support your organisation’s regular patch programmes. Automatically copy over the required patches, shut down relevant applications at the specified change window, and install the patches. After restarting your server(s), trigger post-reboot checks and carry out checks on each patched application. A real-time record of each patching activity as it occurs will provide audit trails for compliance.
Support regular patch programs
Install and check patches where required
Ensure audit trail for compliance
Trusted by leading organisations
Trusted by leading organisations







Tell us about your business and its security requirements
Access your tenant, configure your automation settings and security controls
Create automations - self-serve or with our Managed Automation Service
Begin benefitting from powerful and efficient security automations